Unlock Remote IoT: AWS VPC Network Secrets & Solutions
Is the future of interconnected devices truly secure, or are we building a house of cards on a foundation of vulnerability? The intersection of Remote IoT, VPC Network architectures, and Amazon Web Services (AWS) presents a complex landscape where innovation clashes with the constant threat of cyber intrusion.
The digital revolution has brought forth an era where the "Internet of Things" (IoT) reigns supreme, connecting devices from smart refrigerators to industrial sensors. This connectivity, however, opens doors to significant security challenges. As these devices proliferate, the attack surface expands exponentially, making it increasingly difficult to safeguard sensitive data and ensure operational integrity. The integration of Virtual Private Cloud (VPC) networks within AWS provides a crucial layer of isolation and control, yet it is a landscape that demands constant vigilance and a proactive approach to defense. Understanding the intricate dance between Remote IoT devices, VPC network design, and the robust infrastructure offered by AWS is paramount to securing the connected future. The goal is not simply to build, but to build securely, responsibly, and with a keen eye on the evolving threat landscape. It's a race against time to ensure the benefits of connectivity don't come at the cost of widespread compromise. The challenge lies in creating a robust architecture that can withstand a relentless barrage of threats, evolving with them, and providing a solid foundation for the continued growth of the IoT ecosystem.
The underlying principles of secure network design are critically important to grasp when dealing with the intersection of remote IoT devices, VPC network strategies, and the resources available within AWS. We are talking about a multi-faceted process that begins with careful planning and then proceeds through several layers of defense, all of which must be meticulously implemented and continually monitored. The core of the security framework revolves around isolation, authentication, and access control. Isolating remote IoT devices within a VPC helps to confine potential damage. This prevents an intrusion on one device from spreading laterally throughout the entire network. Authenticating the devices and enforcing strict access controls limit the ability of unauthorized entities to gain access to the network or the data it handles. These steps are not merely suggestions; they are necessary building blocks for a secure IoT environment. Security professionals are continually analyzing the latest threat vectors and deploying measures to protect against them. A proactive, rather than reactive, approach to security is essential. The network configuration needs to be adaptable, and security policies need to be updated in response to new threats, vulnerabilities, and technological advancements. The combination of all these considerations yields a security strategy that is both robust and resilient.
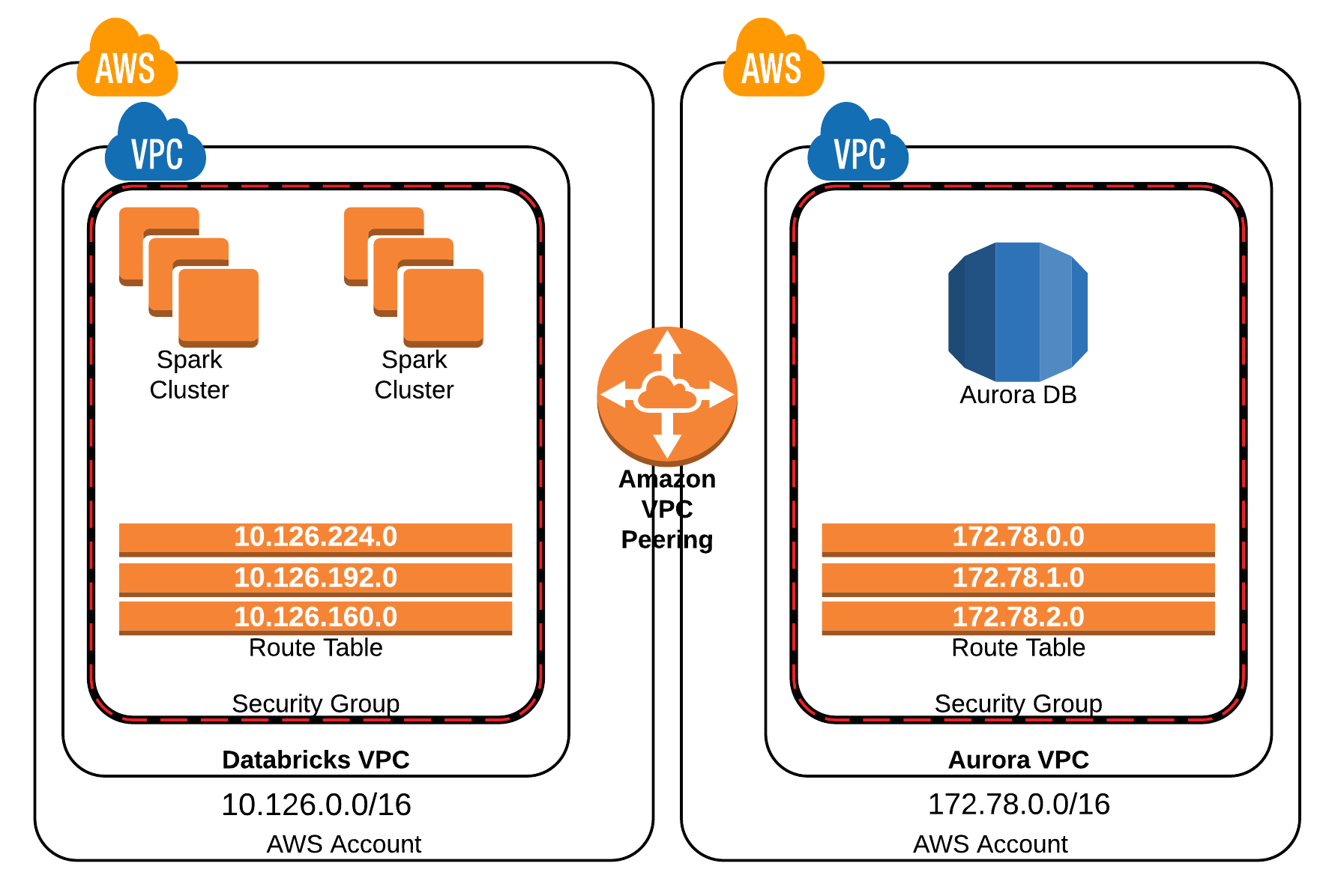
Within an AWS environment, Virtual Private Clouds (VPCs) provide an isolated network environment for your resources, providing an important cornerstone of security. VPCs enable fine-grained control over network traffic, allowing you to establish robust security boundaries and manage your resources with precision. Deploying remote IoT devices within a VPC allows for segmentation of the network, isolating these often-vulnerable devices from other critical infrastructure. This design prevents malicious actors from gaining access to sensitive resources. VPCs enable the use of security groups, which function as virtual firewalls, permitting or denying traffic based on rules. These rules govern ingress and egress traffic, providing a granular level of control over network communications. Network Access Control Lists (ACLs) offer an additional layer of defense by filtering traffic at the subnet level. By carefully configuring both security groups and network ACLs, you can build a layered security architecture that minimizes attack surfaces. Furthermore, VPC endpoints enable secure and private access to various AWS services without traversing the public internet. This architecture helps to reduce the attack surface and enhances performance. VPC Flow Logs record information about IP traffic going to and from network interfaces within your VPC. By analyzing these logs, you can monitor traffic patterns, identify anomalies, and detect potential security threats. These logs can be integrated with security information and event management (SIEM) systems to facilitate comprehensive security monitoring. The careful application of all of these components ensures a safer, more resilient environment for the deployment of remote IoT devices within AWS.
Securing remote IoT devices deployed within a VPC on AWS is not simply about ticking boxes; it's a holistic approach that requires careful consideration of several factors, each essential to the overall security posture. Authentication and authorization mechanisms are fundamental in this context. Implementing strong authentication protocols, such as multi-factor authentication (MFA), ensures that only authorized devices and users can access the network. Furthermore, establishing a robust authorization framework defines the level of access each device and user has. Regularly reviewing and updating these access controls reduces the risk of unauthorized access and data breaches. Encryption plays a vital role in securing sensitive data. Employing encryption both in transit and at rest protects data from unauthorized access, whether it is moving across the network or stored within your systems. Regular encryption key rotation and management procedures further enhance security. Monitoring and logging are essential components of an effective security strategy. Comprehensive monitoring of network traffic, system logs, and device activity allows for the identification of suspicious behavior and potential security incidents. Integrating logging data with security information and event management (SIEM) systems enables prompt threat detection and incident response. Finally, vulnerability management is crucial. Regularly scanning remote IoT devices for vulnerabilities and applying security patches promptly minimizes the attack surface and reduces the likelihood of exploitation. Automating patch management and vulnerability assessments ensures ongoing security and reduces the potential for security gaps. The meticulous attention to these elements forms the groundwork of a strong security posture, making it significantly harder for malicious actors to compromise remote IoT devices within the VPC architecture of AWS.
The challenges of securing Remote IoT in a VPC on AWS are numerous and varied, requiring a comprehensive approach to risk mitigation. One of the most significant challenges is the inherent diversity of IoT devices themselves. They come in countless forms, from simple sensors to complex industrial machinery, and are often developed with differing security standards, creating heterogeneous environments. This creates a broad attack surface, as each device represents a potential point of entry for malicious actors. Patching and updating these devices can be difficult and cumbersome, especially if the devices are deployed in remote locations or have limited resources. Maintaining secure communication channels is another considerable challenge. Many IoT devices communicate over wireless networks, increasing the risk of interception and manipulation. Encryption protocols must be implemented and configured properly. Another challenge arises from the dynamic nature of IoT deployments. New devices are constantly being added to the network, and existing devices are often upgraded or replaced. This requires continuous monitoring, security assessments, and ongoing configuration management. The resource constraints of many IoT devices pose an additional challenge. The limited processing power, memory, and battery life of these devices frequently necessitate design trade-offs that can compromise security. Careful consideration is needed when selecting security protocols and implementing security features. Successfully addressing these challenges requires an architecture that is both flexible and resilient. A multi-layered security approach, combined with proactive threat intelligence, is a crucial component of effective security.
There are several best practices to be aware of in securing Remote IoT within an AWS VPC environment. Firstly, segmentation is critical. Segment your VPC into distinct subnets and isolate remote IoT devices from other critical infrastructure. Use security groups and network ACLs to control network traffic and enforce strict access controls. Secondly, use strong authentication and authorization mechanisms. Implement MFA, and employ robust identity and access management (IAM) policies. Regularly review and update these controls to prevent unauthorized access. Thirdly, encrypt all data in transit and at rest. Use HTTPS, TLS/SSL for secure communication, and encrypt data stored on IoT devices and in cloud storage. Rotate encryption keys regularly. Fourthly, implement comprehensive monitoring and logging. Enable VPC Flow Logs and CloudTrail to monitor network traffic and system activity. Integrate logging data with SIEM systems for threat detection and incident response. Fifthly, conduct regular vulnerability assessments and patch management. Scan remote IoT devices for vulnerabilities, and apply security patches promptly. Automate patch management processes where possible. Sixth, establish robust incident response plans. Develop and regularly test incident response plans to respond effectively to security incidents. Define roles and responsibilities, and communicate with stakeholders promptly. Finally, adopt a defense-in-depth strategy. Implement multiple layers of security controls, including firewalls, intrusion detection systems, and endpoint protection. These practices can help to fortify your architecture against various threats. These recommended practices are the foundation for building a secure and resilient IoT ecosystem.
AWS provides a range of services to help secure Remote IoT deployments within VPCs, offering robust tools and capabilities for comprehensive security management. Amazon VPC is itself a fundamental building block, providing a logically isolated network environment for your resources. You can use security groups to act as virtual firewalls, controlling ingress and egress traffic at the instance level. Network ACLs provide an additional layer of defense at the subnet level. AWS IoT Core is specifically designed for connecting, managing, and securing IoT devices. It provides features such as device authentication, authorization, and data encryption. AWS IoT Device Defender helps to audit your device configurations, identify security vulnerabilities, and detect anomalous behavior. AWS IoT Device Management helps to onboard, organize, monitor, and remotely manage your IoT devices. AWS CloudTrail records API calls and provides detailed information about user activity and resource changes. This information is essential for auditing and security analysis. AWS CloudWatch provides monitoring and alerting capabilities for your resources. You can use CloudWatch to monitor network traffic, system performance, and security events. Amazon GuardDuty provides threat detection by analyzing your VPC Flow Logs, CloudTrail, and other data sources. It identifies potential security threats and alerts you to suspicious activities. AWS Security Hub provides a centralized view of your security posture and helps to manage security findings across your AWS accounts. The integration of these services, and others, makes it possible to create a highly secure and scalable IoT infrastructure. The synergy between AWS services creates a strong security stance.
The future of Remote IoT security within AWS VPCs hinges on a continuous evolution of security practices, alongside innovation in technological solutions. Cloud security is not static. The threat landscape is constantly changing. There must be constant vigilance and adaptation. We can anticipate more automation in security operations, where AI and machine learning play a larger role in threat detection and incident response. This will help to identify and respond to threats more rapidly. There will be a push towards more integrated security solutions that provide comprehensive coverage across all layers of the IoT stack. Zero trust architectures will become more prevalent, emphasizing strict verification for all access requests. With a zero-trust model, we assume that all users, devices, and networks are potentially hostile. The focus is on verifying identity and continuously evaluating trust before granting access to resources. Serverless computing will become increasingly important for IoT deployments, providing scalability and cost efficiency. Security will need to be integrated seamlessly into these architectures. There will be increasing emphasis on security by design, integrating security into the development lifecycle from the beginning. This will ensure that security is not an afterthought. There must be greater collaboration and information sharing between security professionals, vendors, and regulatory bodies. These collaborative efforts will play a crucial role in adapting to the fast-moving threat environment. The continued evolution of these strategies will create a resilient environment for Remote IoT within the AWS ecosystem.
To effectively manage and secure Remote IoT deployments within an AWS VPC environment, here are some key considerations for planning and architecture: Start by clearly defining your security objectives and risk tolerance. Conduct a comprehensive risk assessment to identify potential threats and vulnerabilities. Design a segmented network architecture, isolating remote IoT devices from other critical resources. Implement strong authentication and authorization mechanisms, including MFA and robust IAM policies. Use encryption for all data in transit and at rest. Implement comprehensive monitoring and logging, integrating with SIEM systems for threat detection and incident response. Establish robust incident response plans and regularly test them. Automate security processes where possible, including patch management and vulnerability assessments. Stay up to date with the latest security threats and best practices. Consider the long-term scalability and maintainability of your security architecture. Regular review and refinement of your security posture will be vital. These points are key to building a resilient, secure IoT ecosystem within the AWS cloud.