Secure IoT: Your Guide To Remoteiot VPC Networks
Are you ready to unlock the full potential of your Internet of Things (IoT) devices, ensuring both security and accessibility? RemoteIoT VPC networks offer a groundbreaking solution for creating secure, scalable, and efficient communication channels for your connected devices, regardless of their location.
A RemoteIoT VPC network is, in essence, a virtualized version of a traditional network. It allows your IoT devices to communicate securely over the internet. Think of it as a private highway exclusively for your devices, shielded from the chaos and potential dangers of the public internet. This approach has become a pivotal topic in the world of cloud computing and networking.
As businesses increasingly transition to remote operations and embrace the power of IoT, understanding how to design and implement secure Virtual Private Cloud (VPC) networks is crucial for maintaining efficient and scalable IT infrastructure. RemoteIoT VPCs provide a robust architecture, ensuring your data remains safe and accessible from anywhere in the world.
Now, if you're new to this concept and find it a bit complicated, worry not. The aim is to break down the concepts step by step, allowing you to grasp every element without feeling overwhelmed. Let's delve into the core aspects of RemoteIoT VPCs and how they transform the way we manage and secure our connected devices. This detailed analysis should help you build a solid foundation and ensure smooth implementation. Managing a RemoteIoT VPC network requires more than simply plugging in a few devices; it demands a solid understanding of cloud infrastructure, security protocols, and network design. The RemoteIoT VPC example serves as a practical demonstration of how VPCs can be used to create secure, scalable, and efficient networks for IoT devices.
The rapid growth in the number of connected devices has amplified the need for secure data transmission channels. VPCs provide an effective solution by enabling devices to communicate within a controlled, isolated environment. This is particularly important in today's landscape, where data breaches are more frequent. Furthermore, this article will help you understand the RemoteIoT VPC network example, which has become a critical topic for businesses and developers who want to securely connect Internet of Things (IoT) devices to cloud environments. As the demand for remote connectivity grows, understanding how to design and implement Virtual Private Cloud (VPC) networks for IoT applications is essential. These applications demonstrate the versatility and value of RemoteIoT VPC in enhancing IoT network performance and security.
Heres a breakdown of the core elements:
- What is a RemoteIoT VPC? It's a virtual private cloud specifically designed for IoT devices. It provides an isolated network environment where your devices can securely communicate.
- Why is it important? The key is security and isolation. By using a VPC, you prevent unauthorized access and protect your data from potential threats.
- How does it work? It allows you to divide your devices into logical groups, harden your public interface, and manage your network more efficiently.
With the increasing adoption of IoT technologies, the need for robust security solutions has never been greater. RemoteIoT VPCs provide a powerful way to safeguard your devices and the sensitive data they generate.
This journey will equip you with the tools and knowledge to create your own VPC, enhancing security, improving performance, and ensuring your IoT devices work seamlessly.
VPC enables users to keep areas isolated to perform private workloads. Companies, users, and organizations who are looking for a cost-effective, secure, and scalable method for their IoT devices should focus on using VPC. Whether you're a developer, IT professional, or simply someone interested in IoT and cloud networking, you can learn to create your own VPC. With RemoteIoT VPC, you can securely and directly connect Raspberry Pi and IoT devices from anywhere, just as if they were on a local private network.
You can use RemoteIoT VPC to divide your devices into logical groups or harden your public interface while securing your system.
The RemoteIoT API enables greater automation and integration of RemoteIoT services into your system. Use these web services to access your device from anywhere, allowing you to control and manage your devices more easily. If you cannot find a method to achieve your objective or are struggling to use the API, please contact our support team with any questions you may have.
Why RemoteIoT VPC Matters
The rise of IoT presents both incredible opportunities and significant challenges. Securing IoT devices and managing the data they generate is paramount. Traditional network setups often fall short, leaving devices vulnerable to various cyber threats. RemoteIoT VPCs address these concerns directly.
Heres what makes RemoteIoT VPC essential
- Enhanced Security: By isolating your IoT devices within a VPC, you minimize their exposure to the public internet. This significantly reduces the risk of unauthorized access, data breaches, and other security threats.
- Improved Privacy: VPCs provide a secure and private environment, ensuring that sensitive data generated by your IoT devices remains confidential. This is particularly important for industries that handle sensitive information, such as healthcare and finance.
- Scalability and Flexibility: VPCs are designed to be scalable, allowing you to easily add or remove devices as your needs evolve. They also offer flexibility in terms of network configuration, allowing you to customize your network to meet your specific requirements.
- Cost-Effectiveness: VPCs can be a cost-effective solution for managing your IoT devices. You only pay for the resources you use, which can help you reduce your IT infrastructure costs.
- Simplified Management: VPCs simplify network management by providing a centralized point of control. You can easily monitor and manage your devices, ensuring they are operating securely and efficiently.
RemoteIoT VPC bridges this gap by offering isolated network environments tailored for IoT devices, ensuring data privacy and reducing security risks. The RemoteIoT VPC network example serves as a foundation for secure, scalable, and efficient communication between devices in an IoT ecosystem.
Whether you're a developer, IT professional, or simply someone interested in IoT and cloud networking, this article will equip you with the necessary tools and understanding to create your own VPC. With RemoteIoT VPC, you can securely and directly connect raspberry pi and IoT devices from anywhere, just as if they were on a local private network.
RemoteIoT VPC in Action: Use Cases
The versatility of RemoteIoT VPC makes it suitable for a wide range of applications. Here are a few examples:
- Smart Homes and Buildings: Securely connect smart thermostats, security cameras, and other IoT devices, ensuring that your home automation system is protected from external threats.
- Industrial IoT (IIoT): Create a secure network for industrial sensors and equipment, enabling remote monitoring and control while protecting critical infrastructure from cyberattacks.
- Healthcare: Safeguard patient data collected by medical devices and ensure compliance with healthcare regulations.
- Agriculture: Monitor and manage agricultural equipment, such as irrigation systems and environmental sensors, in a secure and reliable manner.
- Retail: Securely connect point-of-sale (POS) systems, inventory trackers, and other retail devices, protecting sensitive customer data.
Key benefits of RemoteIoT VPC
- Isolation and Security: Create a private network environment for your IoT devices, isolating them from the public internet and protecting them from unauthorized access and cyber threats.
- Simplified Network Management: Easily configure and manage your IoT network, with a centralized point of control that simplifies monitoring, troubleshooting, and scaling.
- Enhanced Data Privacy: Protect sensitive data generated by your IoT devices by ensuring that all communication and data transfer occur within a secure, private network.
- Scalability and Flexibility: Adapt your network to changing needs by easily adding or removing devices and customizing the network configuration to meet your specific requirements.
- Cost-Effectiveness: Optimize your IT infrastructure costs by using only the resources you need and avoiding the expenses associated with traditional network setups.
In conclusion, a RemoteIoT VPC tutorial provides a comprehensive guide to setting up, configuring, and managing VPCs for IoT applications.
The RemoteIoT VPC network example serves as a foundation for secure, scalable, and efficient communication between devices in an IoT ecosystem. If you are diving into the world of Remote IoT VPC network examples, you've come to the right place. This isn't just about setting up a connection; it's about creating a secure, scalable, and efficient network that can handle the demands of modern IoT devices.
Here's a detailed breakdown:
- Network Design and Architecture: The initial phase, encompassing planning the VPC structure, defining subnets, and establishing security groups.
- Configuration and Setup: Steps to configure a VPC, including creating subnets, setting up routing tables, and implementing security measures.
- Security Protocols and Best Practices: Information on implementing robust security measures such as firewalls, encryption, and access controls.
- Management and Monitoring: The continuous operation and monitoring, to manage the VPC efficiently and maintaining its security posture.
The Technical Deep Dive: Building a RemoteIoT VPC
Building a RemoteIoT VPC requires a solid understanding of several key components. Here's a closer look at each:
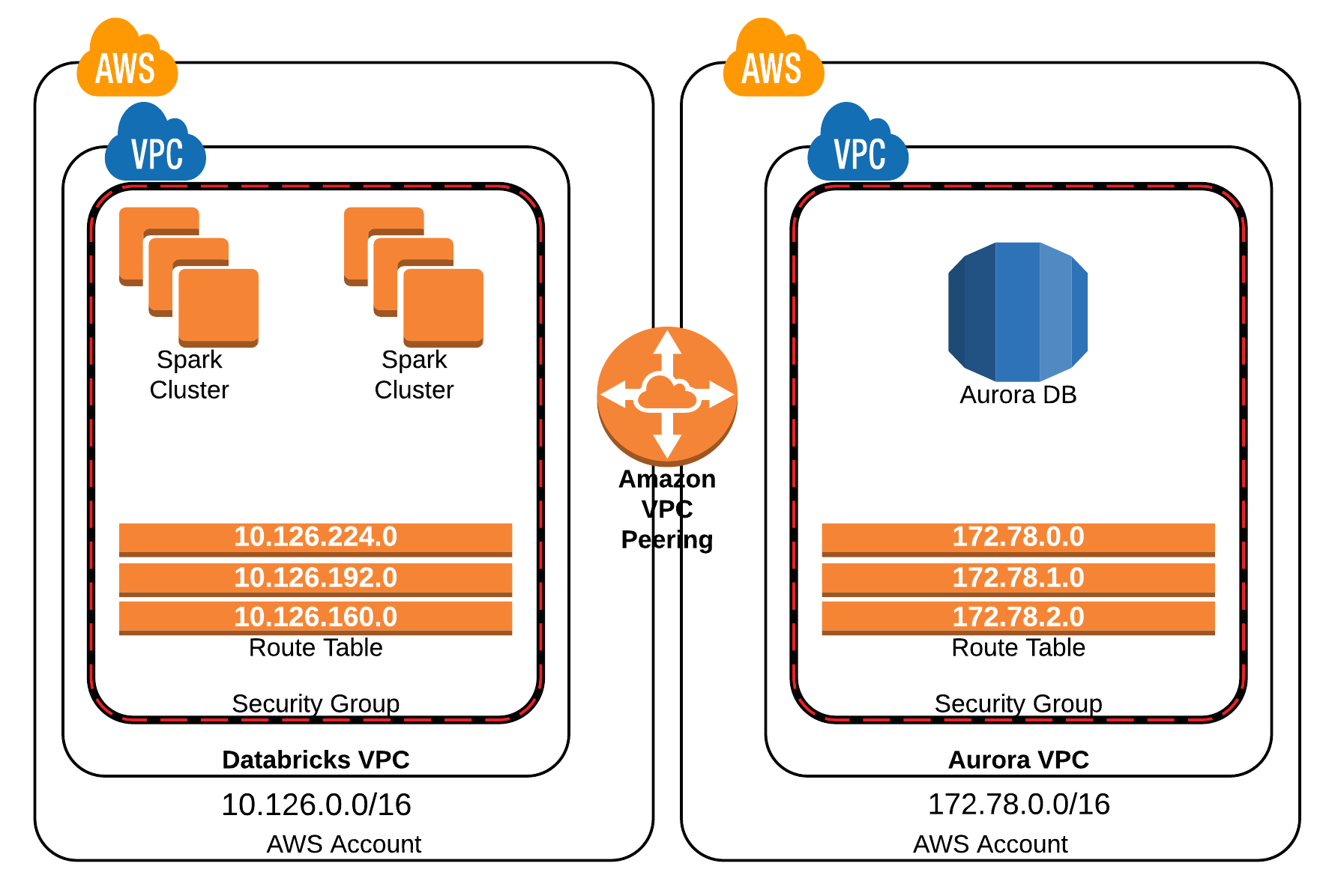
Virtual Private Cloud (VPC): The foundation of your network, a logically isolated section of the cloud where you can launch resources. It's your own private space within the larger cloud infrastructure.
Subnets: Subdivisions within your VPC. You can create public subnets (accessible from the internet) and private subnets (isolated from the internet). This allows for a structured network setup.
Internet Gateway: A gateway that allows your VPC to connect to the internet. It's necessary if you need your devices to communicate with external services.
NAT Gateway/Instance: This is a crucial component for devices in private subnets. It enables them to initiate outbound connections to the internet (for updates, etc.) without being directly accessible from the outside. This enhances security.
Security Groups: Virtual firewalls that control inbound and outbound traffic for your resources. You define rules to allow or deny traffic based on ports, protocols, and IP addresses.
Network Access Control Lists (ACLs): Another layer of security that acts as a firewall at the subnet level. They provide an additional level of control over traffic flow.
Routing Tables: These tables determine the path of network traffic within your VPC. They direct traffic between subnets, the internet gateway, and other resources.
Steps to Implementation
The process of setting up a RemoteIoT VPC typically involves these steps:
- Planning:
- Define your network architecture. Determine the number of subnets, their roles (public/private), and the overall structure.
- Consider your security requirements. Decide on the necessary security groups, access controls, and encryption methods.
- VPC Creation:
- Create your VPC using a cloud provider's console or command-line interface.
- Specify the IP address range for your VPC.
- Subnet Creation:
- Create subnets within your VPC. Consider creating both public and private subnets.
- Assign appropriate IP address ranges to each subnet.
- Internet Gateway and NAT:
- Create an internet gateway and attach it to your VPC.
- If you have private subnets, configure a NAT gateway or instance to allow outbound internet access.
- Security Group Configuration:
- Create and configure security groups to control traffic to and from your devices.
- Define rules to allow necessary inbound and outbound traffic based on ports, protocols, and IP addresses.
- Network ACL Configuration:
- Configure network ACLs to provide additional network security at the subnet level.
- Define rules to allow or deny traffic based on your security requirements.
- Device Deployment:
- Deploy your IoT devices within the appropriate subnets (e.g., private subnets for devices that don't require direct internet access).
- Testing and Monitoring:
- Thoroughly test your network to ensure connectivity and security.
- Implement monitoring tools to track network performance and identify potential issues.
RemoteIoT P2P VPC Network
This is used in specific scenarios and offers several benefits: Granular Accessibility to Network Control, Cost-Effectiveness and the ability for companies to benefit from public cloud resources to scale up or down easily and the ability for users to keep areas isolated to perform private workloads.
Advanced Security Features
To fortify your RemoteIoT VPC network, consider these advanced security features:
- Encryption: Implement encryption for data in transit (using protocols like TLS/SSL) and at rest (using encryption keys) to protect sensitive information.
- Intrusion Detection and Prevention Systems (IDPS): Integrate IDPS to monitor network traffic for malicious activity and automatically block or mitigate threats.
- Multi-Factor Authentication (MFA): Use MFA for all access to your devices and network, adding an extra layer of security.
- Regular Security Audits: Conduct regular security audits and penetration testing to identify vulnerabilities and ensure that your network is secure.
Optimizing Performance and Scalability
To maximize the performance and scalability of your RemoteIoT VPC network, consider these practices:
- Use appropriate instance sizes: Select the right instance sizes for your devices and services to ensure optimal performance.
- Implement load balancing: Use load balancers to distribute traffic across multiple instances, preventing bottlenecks and ensuring high availability.
- Optimize network configurations: Tune your network configurations to minimize latency and maximize throughput.
- Automate scaling: Implement automated scaling to dynamically adjust resources based on demand.
RemoteIoT VPCs are essential for businesses of all sizes. Companies and organizations can also benefit from public cloud resources for easily scaling up or down that business. In today's digital age, remote IoT VPC network setups have become increasingly popular among tech enthusiasts and professionals alike. RemoteIoT VPC network P2P virtual private cloud SSH key management directly connects to Raspberry Pi behind a firewall from anywhere as if it was on the local network. Send commands and batch jobs to Raspberry Pi from web portals. The RemoteIoT API enables greater automation and integration of RemoteIoT services into your system. If you are struggling to use the API, please contact our support team with any questions you may have.
The RemoteIoT API allows even more automation and integration of RemoteIoT service into your system.